Are your OT Devices Protected against cybercriminals?
Published 10 months ago
At E-Panzer, we secure all our client’s OT devices against cybercriminals through a comprehensive security approach. Our solutions include protocol analysis, intrusion detection, vulnerability detection, and behavioral analysis.
OT devices are vulnerable to various cyber threats, including malware, unauthorized access, and data breaches, which can lead to operational disruptions, equipment damage, financial losses, and even safety risks. To protect OT devices, a holistic security strategy is required that addresses the specific risks and vulnerabilities associated with their deployment.
E-Panzer’s Key measures to secure OT devices include:
- Regular patching and updating of devices to address known vulnerabilities.
- Using strong passwords and multi-factor authentication to restrict access.
- Implementing network segmentation to isolate OT systems from other networks.
- Deploying security monitoring tools to detect and respond to attacks.
- Training employees on cybersecurity best practices to identify and report suspicious activities.
- Performing routine security assessments to identify and rectify vulnerabilities.
Additionally, our specialized OT security solutions that can handle the unique requirements of industrial environments, such as low latency and OT-specific protocols, are essential. Solutions like virtual patching can protect unpatched OT devices by preventing the exploitation of vulnerabilities at the network level.
By adopting these best practices and leveraging purpose-built OT security technologies, organizations can effectively defend their OT devices against cybercriminals and ensure the continued safe and reliable operation of their industrial processes.
Some common cyber threats to OT (Operational Technology) devices include:
- Malware infiltration via external hardware and removable media: OT devices are vulnerable to malware infections through the use of infected USB drives, external hardware, and other removable media.
- DDoS attacks and IoT botnets: Poorly secured IoT devices can be hijacked and used as part of botnets to launch Distributed Denial of Service (DDoS) attacks, disrupting the operation of OT systems.
- Human error: Mistakes made by employees, such as misconfiguration of security settings or falling for social engineering attacks, can compromise the security of OT devices.
- Targeted attacks on OT systems: Cybercriminals and nation-state actors are increasingly targeting OT environments, leveraging vulnerabilities in legacy systems and third-party connections to gain access and cause physical damage or disruption.
- Lack of visibility and security controls: Many OT environments struggle with limited ability to monitor and secure their devices due to legacy systems, unclear ownership between OT and IT teams, and business constraints that make it difficult to implement security updates.
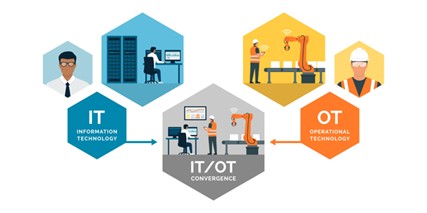
- Convergence of IT and OT networks: The increasing interconnectivity between IT and OT systems creates new attack vectors, as cybercriminals can potentially "jump" from the IT network to the OT network and gain control of critical industrial processes.
Let E-Panzer be your cybersecurity partner
By investing in E-Panzer’s robust defenses, conducting regular testing, updating security plans, and implementing strategies like employee education, multi-factor authentication, data encryption, and system updates, organizations can reduce risks and costs associated with breaches. Proactive risk management and implementing measures across organizations are crucial to prevent financial losses from cybercrime. Let the team at E-Panzer protect your OT Devices against malware, DDoS attacks, human error, targeted attacks, lack of visibility and security controls, and the convergence of IT and OT networks. By implementing these best practices, organizations can effectively secure their OT devices and mitigate the risks posed by cyber threats in the industrial environment. Contact us now!